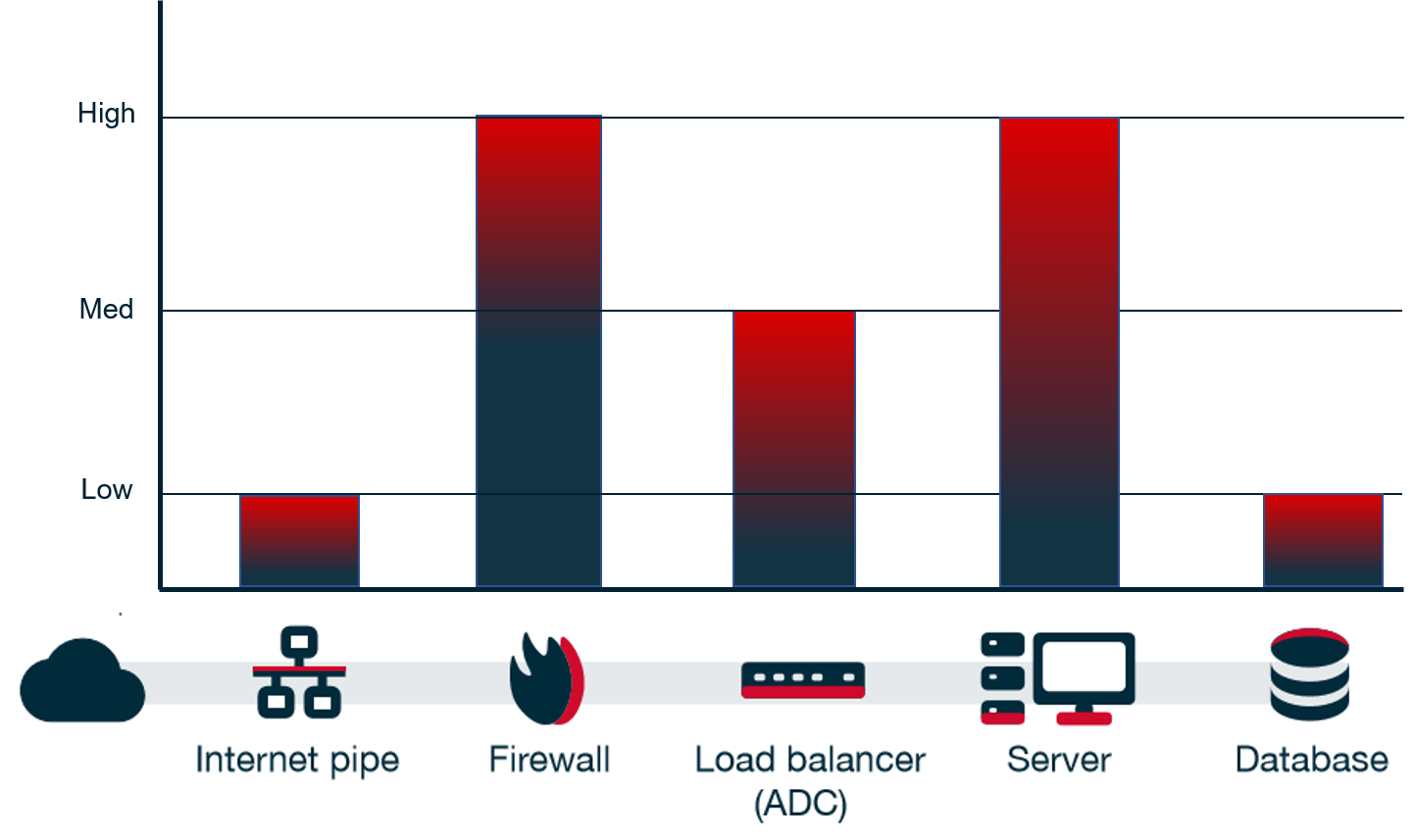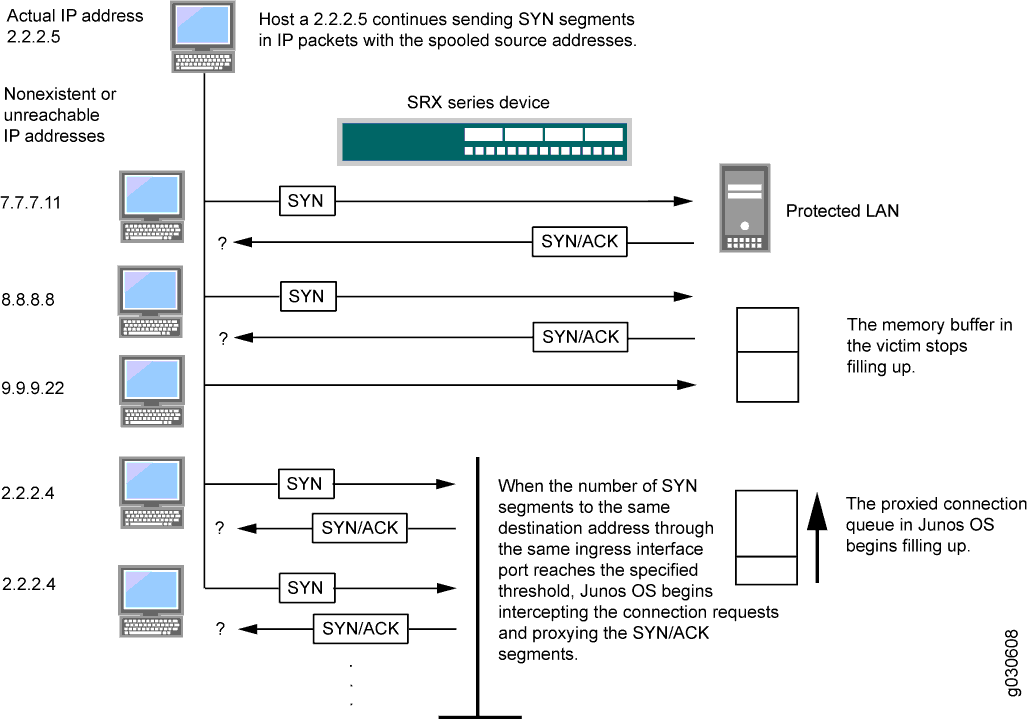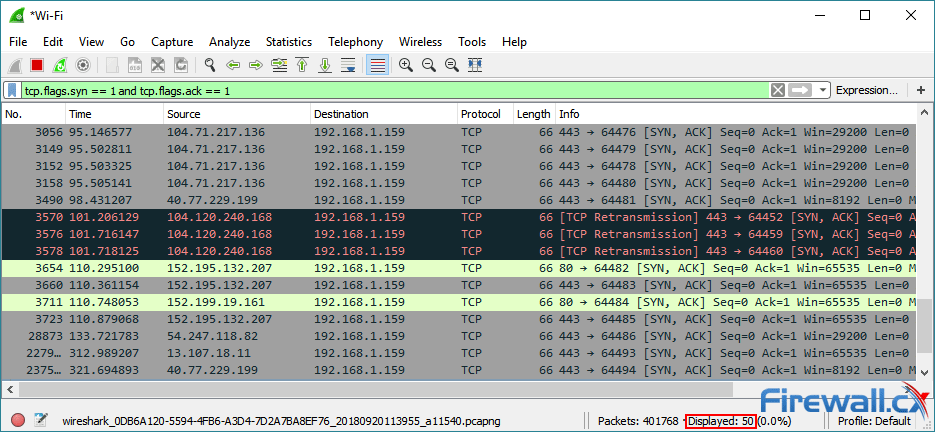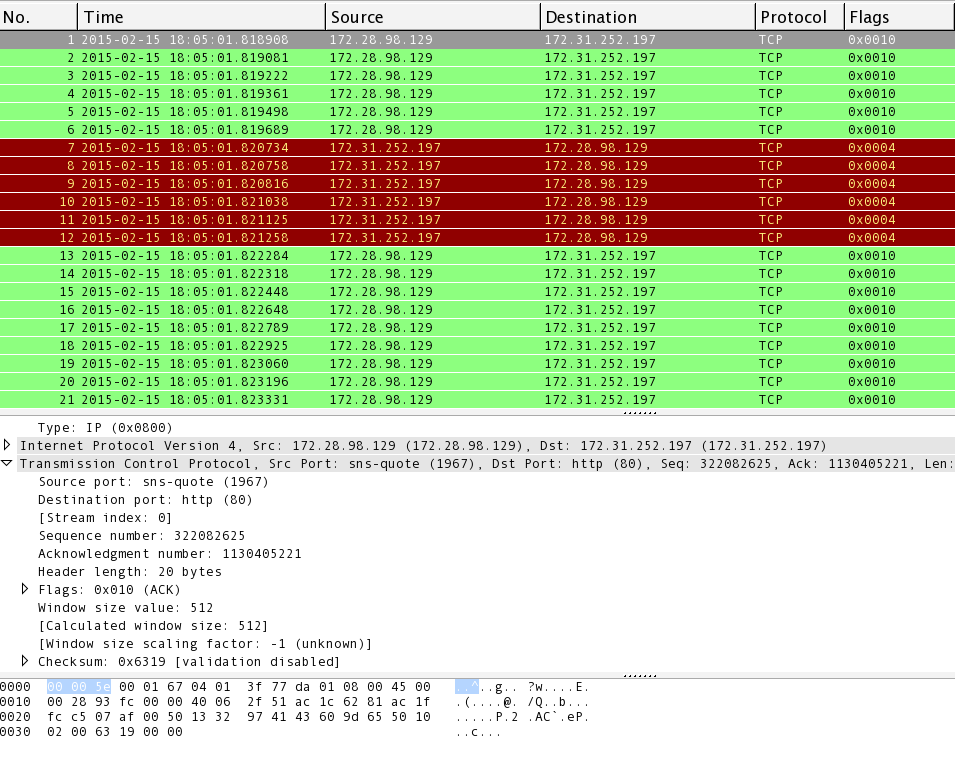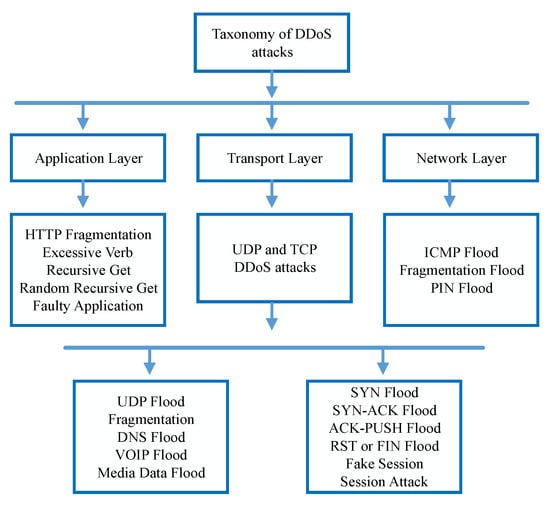
Sensors | Free Full-Text | Adaptive Machine Learning Based Distributed Denial-of-Services Attacks Detection and Mitigation System for SDN-Enabled IoT
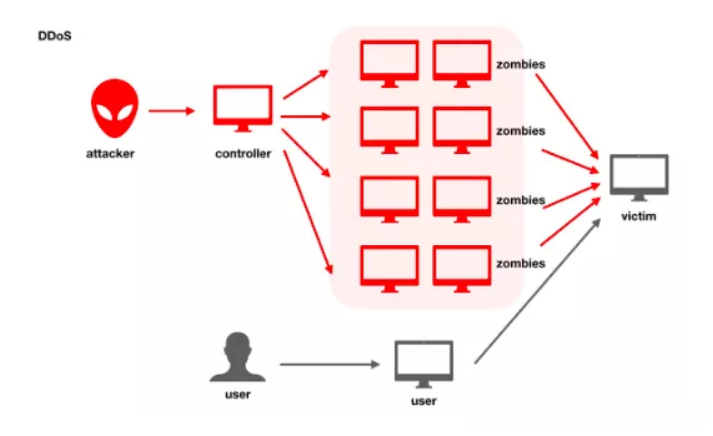
Defending against TB-level Traffic Attacks with Advanced Anti-DDoS systems - Alibaba Cloud Community
Denial of Service (DoS) attack identification and analyse using sniffing technique in the network environment

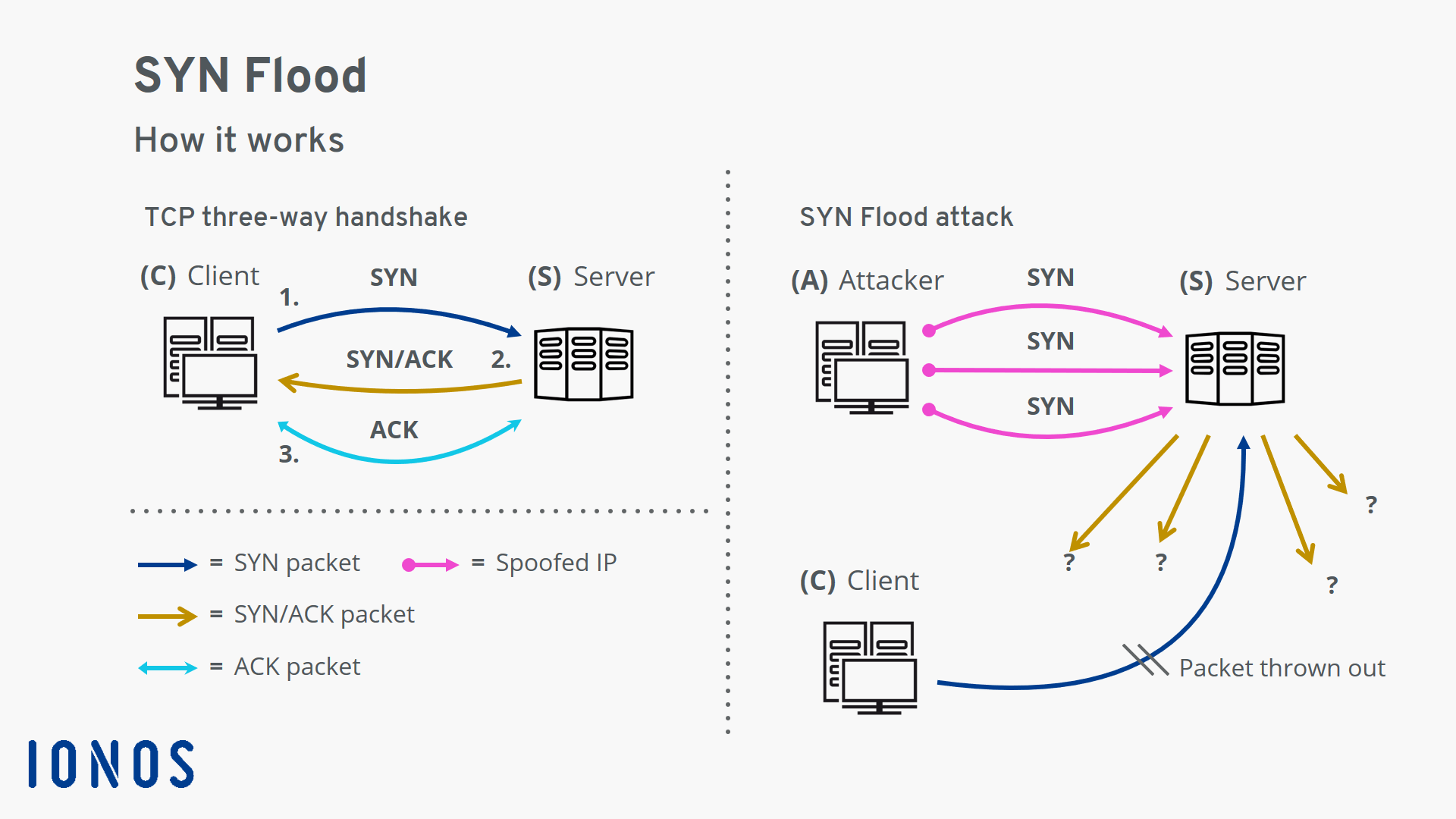
Lightweight Statistical Approach towards TCP SYN Flood DDoS Attack Detection and Mitigation in SDN Environment